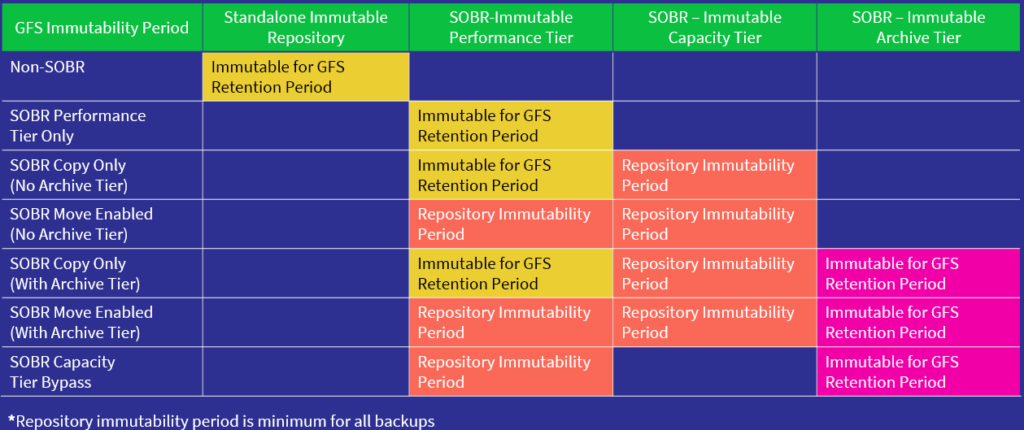
In this blog, I’ll be exploring the new security features that are included in the latest version of Veeam Backup & Replication v12.1, this includes Inline Entropy Analysis, File Index Analysis, and YARA Scanning.
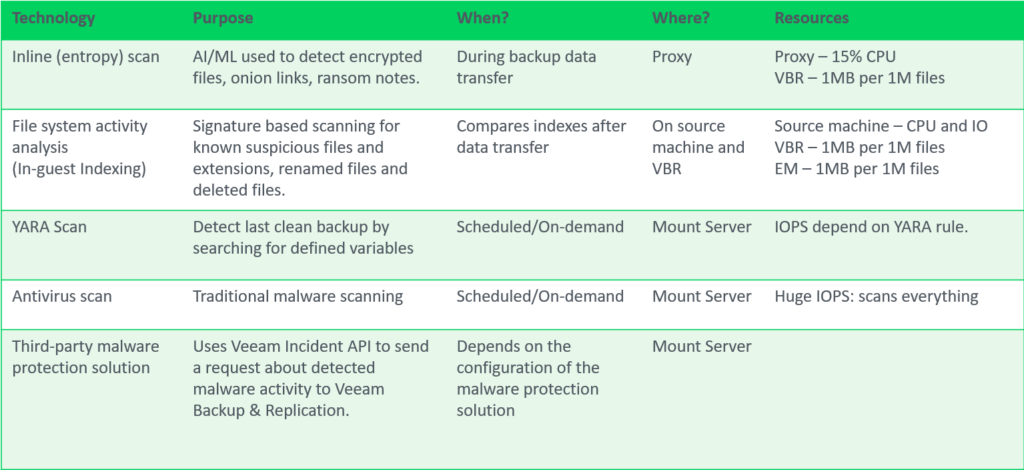
Inline Entropy Analysis
Analyses each source disk block on the fly using an AI/ML-trained model. The scan occurs during every backup run, providing real-time insights into potential anomalies or threats at the block level. Veeam looks for ransomware notes, onion links and data that has recently become encrypted without needing additional software.
Inline analysis is disabled by default, given it’s potential resource consumption so when planning to enable this feature be sure to check if your backup proxies have spare CPU resources, plan for 10-15% additional CPU load per proxy. After enabling, during the first backup run, a full disk scan is performed to create a baseline (not a full backup). It’s possible to exclude machines to reduce the impact during this intial scan using Malware Exclusions.
The sensitivity for inline entropy analysis can be adjusted, it’s recommended to use low sensitivity for environments with heavy encryption usage.
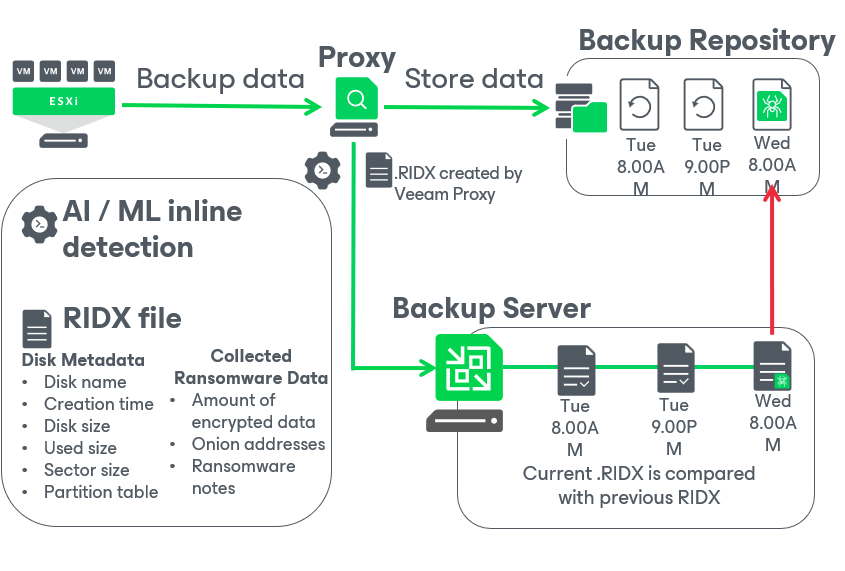
Let’s dive deeper and have a look at a how Veeam inline entropy scanning works once it’s enabled,
Continue reading