The business categorisation feature available in Veeam ONE offers a solution for managing and organising virtual machines (VMs) within virtualised infrastructures, such as stretched cluster environments. By leveraging the underlying ESXi host information, this feature allows IT administrators to create a seamless and dynamic approach to VM management, ensuring optimal backup and recovery strategies.
In a stretched cluster scenario, where VMs can move between different data centres for improved availability and disaster recovery capabilities, the ability to group VMs based on their current location can be quite important. For example, if there is a need to ensure transient VMs are protected to a local backup repository.
Leveraging Veeam ONE’s business categorisation means we can tag VMs according to the specific ESXi host they are running on. Tags can then be configured as the source for a Veeam backup job.
Step 1. Create the category,
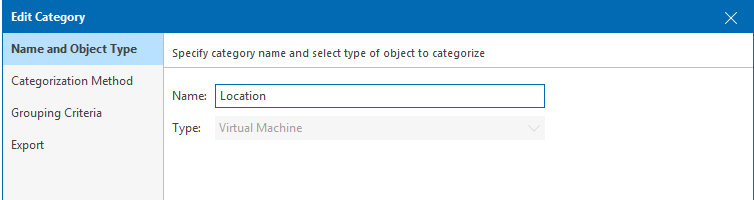
Step 2. Pick ‘Grouping expression’ as the Categorisation method.
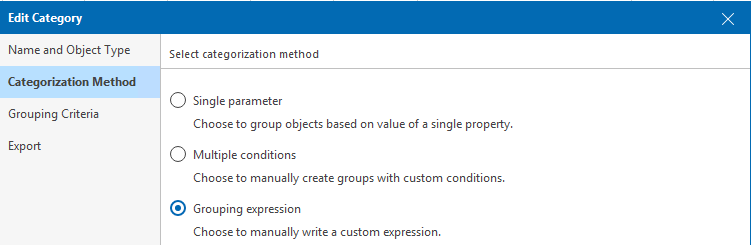
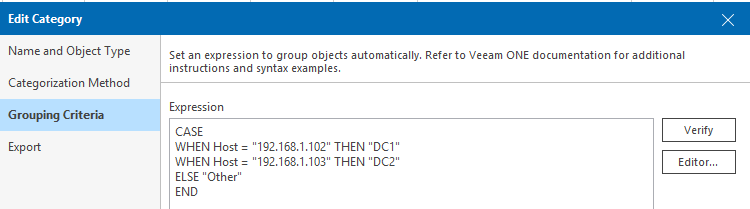
Step 3. Define the expression, in my small home lab I defined the name of the ESXi hosts as they appear in vCenter/VeeamONE.
Step 4. Make sure ‘Create vSphere Tags’ is enabled.
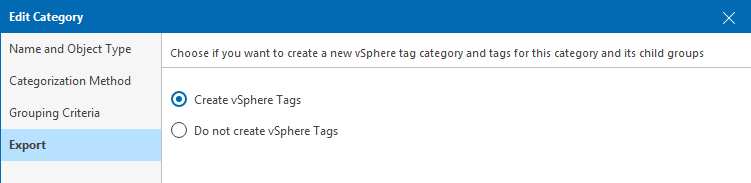
This tagging mechanism creates a clear association between VMs and their respective data centre locations, facilitating efficient backup and recovery strategies tailored to the specific environment.
The vSphere tags are added to the VMs during the Veeam ONE data collection, to ensure vSphere tags are up-to-date, it’s recommended to run the data collection schedule prior to the scheduled backup job or on a regular basis.
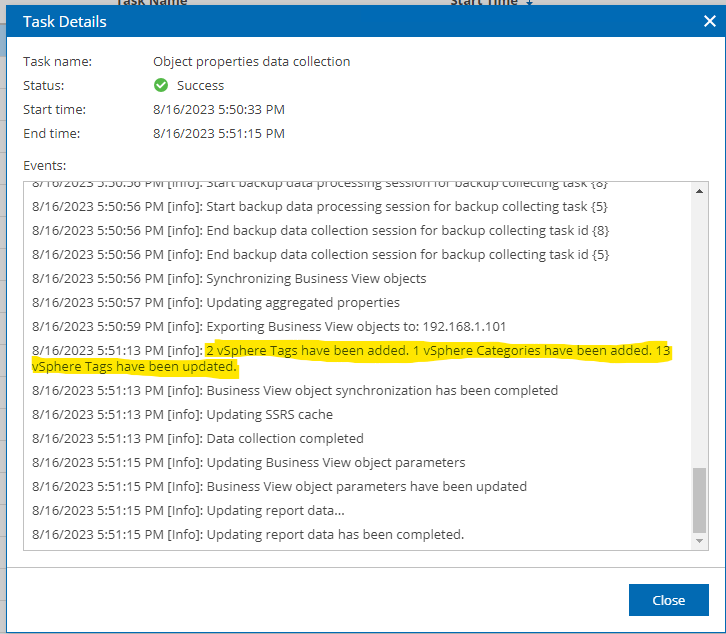
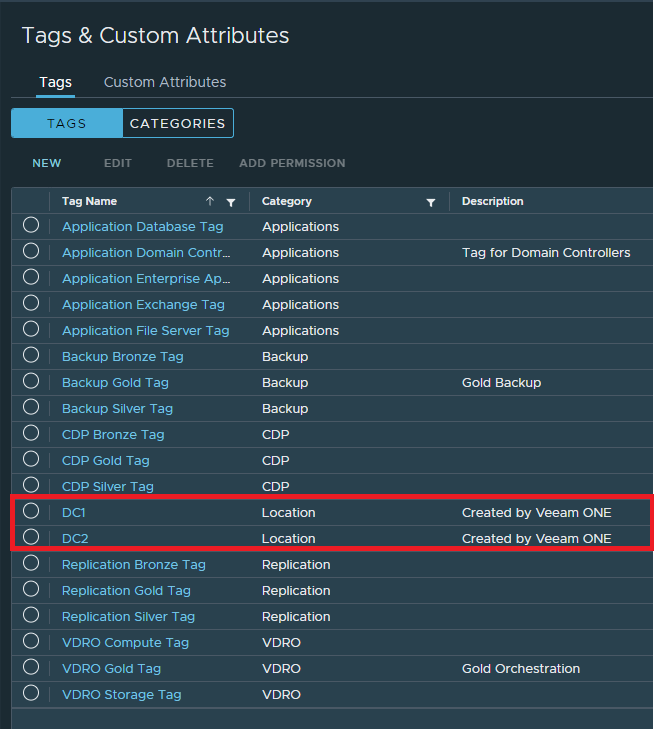
By leveraging Veeam ONE’s business categorisation, when a VM is migrated from one data centre to another, the VMs tag will be updated to reflect the new ESXi host location. This dynamic adjustment ensures that backup jobs remain aligned with the VM’s current data center, enabling the VM to be protected by the appropriate local backup repository. This not only optimises backup performance by avoiding unnecessary data transfers over the stretched cluster’s interconnect but also enhances the overall data protection strategy by adhering to the locality of data.